Passive Subdomain Enumeration: Uncovering More Subdomains than Subfinder & Amass
Subdomain Center notes over 200 competitors, yet Amass integrates 87 and Subfinder 45; this article explores better subdomain enumeration tools.

As the founder of Subdomain Center, the world's largest subdomain database, I've observed that over 200 entities offer freemium access to their web search, DNS, and subdomain datasets. However, tools like Amass and Subfinder have incorporated only a limited number of these passive sources - 87 and 45, respectively. In this article, we will delve into cutting-edge solutions that have the potential to surpass Subfinder and Amass by leveraging broader data integration and advanced techniques for subdomain discovery.
Background
Identifying subdomains is crucial not only for safeguarding internet-exposed assets but also for various other purposes. For instance, an entrepreneur might use it to uncover all educational platforms hosted on Teachable or all stores operating on Shopify, while a crypto enthusiast may monitor new websites for potential airdrop campaigns.
Personally, I began subdomain enumeration as part of bug bounty research, but nowadays, I leverage it to sell findings to cybersecurity companies, researchers, CERT agencies, and others who require such insights.

Regardless of the diverse use cases and varying levels of expertise, individuals who enumerate subdomains universally expect comprehensive visibility. No one is willing to settle for limited freemium sources.
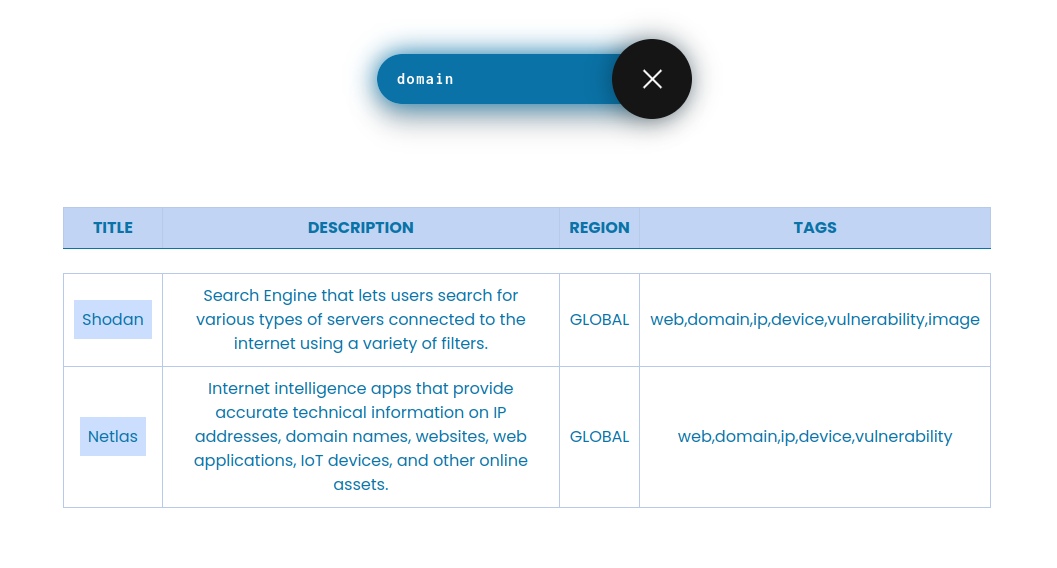
Subfinder and Amass are among the most popular open-source subdomain enumeration automation engines available to us. They individually have managed to integrate 40+ independent APIs such as Censys, Security Trails, Netlas, etc.
However, Subfinder, despite being most widely used automation engine for monitoring subdomains, has lately struggled to keep pace with the growing number of independent sources available.
Subfinder VS Amass
Let compare these two tools, the first table give information about the maintainer:
| Subfinder | Amass | ProjectDiscovery - Delayed integration - High standards - Well funded - 93 contributors |
OWASP - Proactive integration - Average standards - Under resourced - 57 contributors |
|---|
The second breaks down sources:
| Subfinder | Amass | alienvault, anubis, bevigil, binaryedge, bufferover, builtwith, c99, censys, certspotter, chaos, chinaz, commoncrawl, crtsh, digitalyama, digitorus, dnsdb, dnsdumpster, dnsrepo, facebook, fofa, fullhunt, github, gitlab, hackertarget, hudsonrock, hunter, intelx, leakix, netlas, quake, rapiddns, reconcloud, redhuntlabs, riddler, robtex, securitytrails, shodan, sitedossier, threatbook, threatcrowd, threatminer, virustotal, waybackarch, whoisxmlapi, zoomeye | ahrefs, alienvault, anubis, bevigil, bgptools, bgpview, bigdatacloud, bufferover, builtwith, c99, chaos, circl, detectify, dnsdb, dnslytics, dnsrepo, fullhunt, github, gitlab, grepapp, greynoise, hunter, intelx, ipdata, ipinfo, leakix, mnemonic, netlas, onyphe, passivetotal, pentesttools, pulsedive, quake, searchcode, shodan, socradar, spamhaus, sublist3r, threatbook, threatminer, virustotal, whoisxmlapi, yandex, zetalytics, zoomeyecertspotter, 360passivedns, abuseipdb, arquivo, ask, askdns, asnlookup, baidu, binaryedge, bing, censys, certcentral, commoncrawl, crtsh, deepinfo, digitorus, dnsdumpster, dnshistory, dnsspy, duckduckgo, facebook, fofa, gists, google, hackerone, hackertarget, haw, hyperstat, maltiverse, pastebin, pkey, rapiddns, riddler, searx, securitytrails, sitedossier, spyonweb, subdomaincenter, synapsint, ukwebarchive, urlscan, wayback, yahoo |
|---|
Ideally, the best solution to address this oversight would be to be on a lookout for new APIs by yourself and develop an in-house automation system that individually queries these sources. There is at least one new freemium source coming out each month. And each of them has better insights over certain regions like Zoomeye offers better coverage over Chinese domains, CriminalIP is great for domains popular in South Korea and Yandex outperforms for Russian domains.
Moreover, there are a few more promising alternatives to Subfinder & Amass. They are the rising stars in this field excelling at proactively integrating new APIs, allowing users to easily discover new subdomains without any hassle.
Subdominator
Subdominator is a tool developed by Revolt Securities for bug hunting and reconnaissance, focusing on passive subdomain enumeration. It helps cybersecurity professionals discover potential security vulnerabilities by efficiently identifying subdomains using various free passive resources. (~50 best freemium passive sources)
Bighuge BLS OSINT Tool
BBoT is a OSINT framework developed by Black Lantern Security (BLS) designed for gathering information about a target, which may include subdomain enumeration, port scanning, service detection, email enumeration and identifying technologies used. (~60 best freemium passive sources).
A few years ago, a highly professional and humble individual from their company reached out to me, impressed by Subdomain Center. Over my nine years in cybersecurity, I’ve interacted with numerous OSS tool maintainers, and I must say, the people advancing this project are driven by sheer curiosity and passion.
They even attempted to reverse engineer the algorithm behind the enumeration engine we use for Subdomain Center but were unable to succeed due to a lack of access to large datasets. Despite this, their engine remains unparalleled, offering superior coverage and capabilities. It’s truly one of a kind, and I highly recommend checking them out.

Conclusion
I hope you found this article helpful. Additionally, if you are interested in exploring more Open-Source Intelligence (OSINT) resources relevant to your use-case, feel free to checkout my Awesome Intelligence Collection.
Expert and technological input is essential, even if not sufficient. We should think of ourselves as an artist preparing a mosaic. Experts provide tiles. But the job remains ours to utilize those tiles as needed in the process of forming our image. Fundamentally, we need to think for ourselves. - Dr. Vikram Mansharamani



